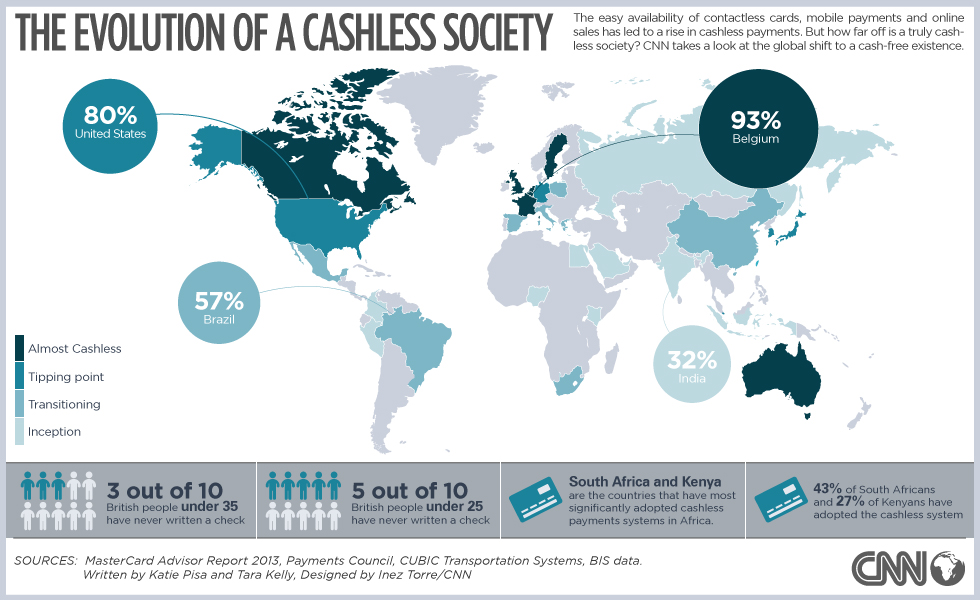
Source: CNN
A cashless society is no longer a myth but an impending reality, one of the causes for concern is the issue of privacy which this article deals with.
The idea of a cashless society, i.e., ‘a civilization holding money, but without its most distinctive material representation – cash’, is said to have originated in the late 1960s. The transition to go cashless had been slow and steady, but it is now increasing at a rapid pace this last decade. As technology evolves, the shift from a cash reliant to a cashless society is becoming more apparent. At least in the urban society, using ‘contactless payments’ or ‘non-cash money’ is not unheard of. It has been reported that not only did the first debit card possibly hit the markets in the mid-1960s but that in 1990, debit cards were used in about 300 million transactions, showing the rise of the same in today’s society. Before welcoming this change with open arms, we must take care that we do not ignore the security and privacy concerns, some of which will be addressed in this article.
As we are transitioning from a cash-reliant society to a [quasi] cashless society, there are some fears about phones being hacked or stolen, or reliance placed on devices which require batteries or internet – what if either is not available? However, conversely, our cash or wallets could be stolen, destroyed in a matter of seconds, could be misplaced, etc. The only difference is the medium of transaction.
Fear is a factor which inhibits change, however these fears are usually not unfounded. In the year 2014, Target, the second-largest discount store retailer in the United States was hacked and up to 70 million customers were hit by a data breach. Furthermore, 2 years later, it was reported that roughly 3.2 million debit cards were compromised in India, affecting several banks such as SBI, ICICI, HDFC, etc.
Nevertheless, as earlier pointed out, just as financial details present online can be stolen, so can paper money. With each transaction taking place online, the fears of online fraud are present, however Guri Melby of Liberal (Venstre) party noted, “The opportunity for crime and fraud does not depend on what type of payment methods we have in society.” A mere shift in the means of trade will not eliminate such crimes. It is here that I must clarify that a cashless society could be in various forms and degrees, be it debit/credit cards, NFC payments, digital currencies such as bitcoin or even mobile transactions such as M-Pesa.
Bruce Schneier, cyber security expert and author of best seller, Data and Goliath, notes that the importance of privacy lies in protection from abuse of power. A hegemony of the authorities over our information – details [and means] of our every transaction – provides absolute power to the authorities and thus a much higher scope for abuse. Daniel Solove, further notes that abuse of power by the Government could lead to distortion of data; however, even if we believe the government to be benevolent, we must consider that data breaches and hack could (and do) occur.
Cash brings with it the double-edged sword of an anonymity that digital transactions do not provide. A completely cashless society might seem attractive in that each transaction can be traced and therefore possibly result in reduction of tax evasion or illicit and illegal activities; however, though that crime might cease to exist in that form, it could always evolve and manifest itself in some other form online.
One of the concerns raised in this regard is that the government could indefinitely hold or be in possession of our transaction history. This seems to be an innocent trade-off for the ease and convenience it provides. The issue that arises however, as Domagoj Sajter notes, is that every single citizen has become a potential criminal and a terrorist to the government, worthy of continuous and perpetual monitoring. The citizens become latent culprits whose guilt is implied, only waiting to be recorded and proven. The principle of innocent till proven guilty vanishes in the mind of the government.
Furthermore, a completely cashless society places power with the Government with no checks and balances of the same. Advanced technology could disable funding of mass actions, extensive protests and large-scale civil disobediences, all of which are important traits of democratic processes. It is pertinent to remember that Martin Luther King Jr. was tracked by the FBI. Providing the government with more ease in curtailing democratic processes leads to a more autocratic governance.
Consider the following: an individual finds out that the Government or one of its agencies is committing a crime against humanity, and she reports it to the public. Not only could her personal life be excavated to find faults but any support that she would receive in terms of money (in a cashless society) could possibly be blocked by the Government. Minor faults could be listed and propaganda could be spread to discredit her point or deviate the masses’ attention. By controlling the economy, they could wring the arms of the media and force them to not focus on or to ignore the issues raised by her.
Michael Snyder also raises an important point about erasure of autonomy in a cashless society, “Just imagine a world where you could not buy, sell, get a job or open a bank account without participating in ‘the system’”. It need not start with forcing people to opt-in, simply providing benefits in some form could indirectly give people no choice but to opt-in. The Supreme Court of India has noted multiple times that the Aadhar Card cannot be made compulsory (a biometric identity card). However, the Aadhar card has been made mandatory to avail EPF Pension Schemes, LPG Benefits and even for IIT JEE 2017. The Government of India is even mulling making Aadhaar number mandatory for filing of income tax (I-T) and link all bank accounts to the unique identity number by the end of this financial year. The government is concurrently working on developing a common mobile phone app that can be used by shopkeepers and merchants for receiving Aadhaar-enabled payments, bypassing credit and debit cards and further moving to cashless transactions. The Aadhaar-enabled payment system (AEPS) is a biometric way of making payments, using only the fingerprint linked to Aadhaar. These are all part of the measures taken by the Indian government to brute force the Indian economy into a cashless form.
Policing of the citizen is not a purely hypothetical scenario; it has already taken place in the past. In 2010, a blockade was imposed by Bank of America, VISA, MasterCard and PayPal on WikiLeaks. In 2014, Eden Alexander started a crowdfunding campaign hoping to cover her medical expenses, but later, the campaign was shut down and the payments were frozen; the cause being that she was a porn actress. We must also take into account the empowerment that cash provides; consider an individual saving cash from their alcoholic or abusive spouse, or the individual who stuffs spare notes under her mattress for years because it gives her a sense of autonomy. We should take care that in seeking development, we do not disempower the downtrodden, but lift them up with us.
The idea of a cashless society is no longer strange, with multiple corporations and even countries having expressed their interest in going cashless. Harvard economist and former chief economist of the IMF, Kenneth Rogoff in his Case Against Cash argues that a less-cash society [in contradistinction to a cash-less society] could possibly reduce economic crime, he suggests in the same article that this could be executed by a gradual phasing out of larger notes. A cashless or less-cash society is inevitable. In Sweden, cash transactions made up barely 2% of the value of all payments made. The question thus is not about when [it will happen] but what are the safeguards we set up to protect our rights.
For further reading:
1] Melissa Farmer: Data Security In A Cashless Society
https://www.academia.edu/12799515/Data_Security_In_A_Cashless_Society
2] David Naylor, Matthew K. Mukerjee and Peter Steenkiste: Balancing Accountability and Privacy in the Network
https://www.cs.cmu.edu/~dnaylor/APIP.pdf
3] Who would actually benefit from a Cashless Society?
https://geopolitics.co/2016/01/30/who-would-benefit-from-a-cashless-society/
4] Anne Bouverot: Banking the unbanked: The mobile money revolution
http://edition.cnn.com/2014/11/06/opinion/banking-the-unbanked-mobile-money/index.html
5] Kenneth Rogoff: Costs and benefits to phasing out paper currency
http://scholar.harvard.edu/files/rogoff/files/c13431.pdf
