[This piece has been authored by Anushruti Shah, a fourth-year law student at the Hidayatullah National Law University, Raipur]
Introduction
It is relatively unknown, but brain implants and other neural devices have been effectively utilized for quite a long time to treat neurological and brain injuries. Such devices claim of enhancing the quality of our life and eventually expanding the utility of our brains. For instance, last year Neuralink Corporation, the American neurotechnology company founded by Elon Musk, unveiled its animal trial in a video featuring a pig called Gertrude with a computer chip inside its brain, to demonstrate the company’s plans to create a brain-to-machine interface. The company aims to build an interface that would connect the human brains with machines, and recently it released a video of a primate, who had been implanted with its technology, playing the game “Pong” with its thoughts. Futurists and AI Experts visualize a future where synthetic brains will, in the coming future, expand the functionality of our brain where it could surpass the power of an organic human brain.
Simultaneously, humans seem to have no boundaries when it comes to finding multiplicity of ways to attack new devices. Such people have already hacked into mobile phones, online websites, social media platforms, ATMs, and many such places. If such brain implants accomplish their claims, their usage will expand in the future. When this happens, a wide variety of legal, safety, and policy concerns would arise. This article talks about such brain implants and delves into their technological intricacies in order to ascertain the nature of the data collected, stored and processed by them to find out why such data requires protection in the future, while also discussing the data privacy issues that will emerge from it.
What is a Brain Implant?
Brain implants which are often stated as neural implants are devices that are directly connected to a biological subject’s brain. The common purpose of brain implants and the focus of recent research is on establishing artificial areas in the brain parts that have become dysfunctional. This involves sensory replacement, e.g., vision. Some brain implants involve creating interfaces between neural systems and computer chips. This work is part of a wider research field called brain-computer interfaces. These Brain-Computer Interface (BCI) or Brain-Machine Interface (BMI) devices have been under research and development for a very long time, where some devices have already arrived in the market.
The possibilities offered by brain-computer interfaces are almost infinite: gaming, motor control, health, and transportation, among others. This is why a large number of companies have detected this niche and are on board. From large companies such as Nissan with its brain-to-vehicle technology, Facebook with its “mental keyboard”, Microsoft with its new patents, and new startups with millionaire funding such as Neuralink by Elon Musk and Kernel by Bryan Johnson. Numerous research projects are in progress to develop such technologies and Neuro-prosthetic devices. In the forthcoming years, it is quite evident that we will continue to develop, sell, and use such devices. Nonetheless, over the coming decades, such devices exhibit the potential to dramatically enhance the functioning of the brain and eventually transforming the Neuro-medical sector.
General Overview of Types of BCI
The types of BCI can be widely differentiated by the degree of invasiveness to individual body and in the method used to measure brain activity. In particular, these differences are of special interest because the information (data) extracted and stored by this technology broadly diverge from each other in term of quantity and quality of data. A distinction is usually made between invasive and non-invasive BCI (Refer to Point 4).
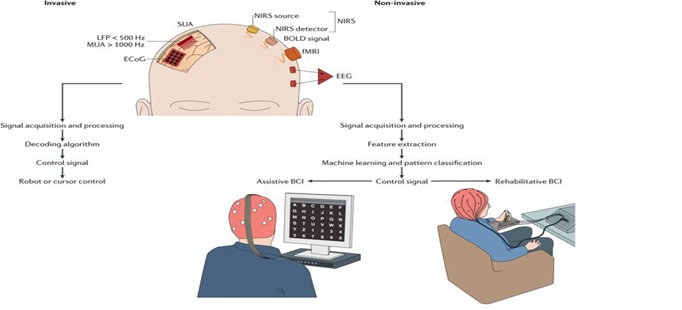
Image source: Chaudhary, U., Birbaumer, N. & Ramos-Murguialday, A. Brain–computer interfaces for communication and rehabilitation. Nat Rev Neurol 12, 513–525 (2016).
The Invasive technique requires surgery to implant the necessary sensor in order to record the brain activity. However, drawbacks such as limited usability due to surgery requirements, a risk of infection due to long-term use of the device, financial costs, and ethical considerations outweigh such benefits. As a result, this type of BCI is commonly limited to the medical field (Refer Pg. 4).
The Non-invasive technique offering an alternative to natural communication and control are various (Refer Pg. 6). The most important neuroimaging technique for BCI utilization are magnetoencephalography (MEG) which measures magnetic fields produced by electrical current occurring naturally in the brain, functional magnetic resonance imaging (fMRI) which recognize the changes in blood flow determined by the neural activity in the brain and the functional near-infrared spectroscopy (fNIRS) which, through the use of light in the near-infrared range, map blood dynamic in the brain in order to detect neural activity. Lastly, but most importantly, Electroencephalography (EEG) which records brain activity as electrical signals, using electrodes placed around the scalp.
These non-invasive techniques differ not only in terms of how they record brain activity, but also in terms of portability and imaging capabilities, all of which have an impact on the information that the BCI can collect.
EEG offers a higher temporal resolution, portability capacity, and a low level of technical requirement, making it suitable for commercial use (Refer to Point 5). Because the EEG method’s characteristics make such a device inexpensive, portable, and simple to use, this article focuses solely on this type of BCI. Furthermore, because the EEG is more commercially viable than other neuroimaging techniques, the possibility of disseminating a massive amount and variety of brain data is much more feasible.
Working of BCI by the EEG Method
The processing and storage of brain data has recently become easier than ever before, thanks to the introduction of low-cost, user-friendly BCI devices based on the EEG method, which are further combined with powerful mobile devices, software programmes, and cloud services. (Refer to Point 8. BCI Applications)
Several companies offer this type of consumer-grade device that can be used for a variety of applications, such as video games and hands-free keyboards, as well as application stores (AppStores) similar to those found on smart phones, where application developers can also access brain data to deliver their services [See 31]. It’s also possible to imagine databases of EEG data collected from these app store users for the purpose of providing services and developing applications.
In simple terms, our brain is made up of cells called neurons. These neurons which are active due to Biochemical and electrical signals are at work whenever we think, move, feel, remember something or perform any other activity. Using EEG technology, scientists can detect those signals and interpret what they mean. EEG is capable of reading signals from the human brain and sending them to amplifiers. A BCI computer program interprets the amplified signals and uses them to control a device.
A BCI based on EEG technique has, apparently, a simple structure composed of six operations. The first step involves the measurement of brain activity in order to acquire the raw signals of the individual. In the second step, specific filters are applied to the raw signals to reduce noise caused by muscles movements so that a better signal is extracted in the third phase. The extracted signal (also called feature) is then classified (fourth step) and translated into a command recognizable by the machine (fifth step). Usually, feedback is provided to the user in the last step to inform him/her of the recognized brain activity pattern (sixth step). The acquisition of EEG is the first step in the functioning of BCI.
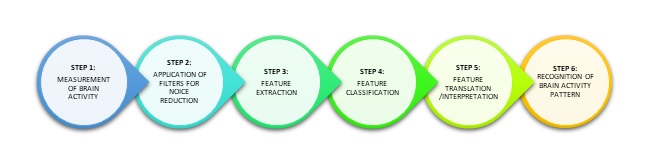
Characteristics of EEG Data and Why Protection is Necessary
EEG data is an extremely rich signal which may capture significant brain activity of the user. As technology continues to evolve, it is just a matter of time before that more and qualitative better information will be extracted and analyzed. Traces collected by EEG signal can be used in the medical field for prevention, detection and diagnosis, starting with the most sensitive information that the individual voluntarily discloses.
EEG recording can also be used for identification and authentication of users. It has been shown that a characteristic of EEG signal is to be unique for every individual, meaning that any two persons have different EEG signal, which is stable over time and resistant to experimental change in both closed eyes and open eyes conditions. Thus, different experiments then successfully demonstrated that such EEG characteristic can be used for either identification (with an accuracy of 80-100%) or authentication purpose.
What’s important to remember is that such sensitive data can be obtained with a small number of electrodes and a non-invasive, relatively inexpensive method. Even against the will or awareness of individuals, reveal more sensitive information such as PIN numbers, dates of birth, religious and political beliefs.
Surprisingly, using such a technique allows for the efficient collection of the most sensitive data, as an involuntary response is stronger when a stimulus recalls the most important aspects of a person’s past experience. To put it another way, the more a stimulus is linked to an individual, the easier it is to capture sensitive information because the BCI captures a sharper response. These security problems are considered so tangible that they have forced scholars from different backgrounds to call for an interdisciplinary approach and to develop technical means to tackle neuro-security problems (i.e. the protection of neural devices from malicious attackers trying to exploit, block, eavesdrop or generally endangering the safety of users), while other scholars already attached the label of a new generation type of cybercrime.
What Does this Mean for the Data Market?
The fact that a BCI’s output is dependent on an input of brain activity/data necessarily raises the question of how and to what extent such technology detects, reads, stores and processes such data. This is a necessary step in determining whether personal data is collected and, if so, whether data protection laws such as GDPR can be used to limit the indiscriminate dissemination of brain data.
As seen above, general brain activity recordings may be reconstructed into purpose-specific information during processing. In principle, multiple processing of the same general brain recording for different purposes could yield different information. This indicates that data is being used in ways that warrant closer examination from a data protection standpoint.
Because of GDPR’s global ambitions, the author limits the current discussion of data protection regulation to the European General Data Protection Regulation (GDPR) which is a paradigmatic case of data protection legislation.
Does Brain Data Fall within the Scope of GDPR?
In determining whether activities of BCI fall within the scope of GDPR, two elements must be evaluated.
- The data must be ‘processed’: Data processing is a broad term that encompasses most of the operations that are likely to occur during the collection and storage of brain data. In terms of this dimension of the regulation, it seems clear that any conceivable BCI will certainly process data in a regulation-relevant way.
- The data must be ‘personal’: The GDPR takes a relatively rigid approach in its application, and determining whether data are personal or not is a crucial element in it. That is, either the law applies completely if the data are determined to be personal data or it falls outside of regulation when it is not.
Article 4(1) read with Recital 30 of the GDPR indicates that technical identifiers may be considered personal data when they provide a link to natural person. However, a technical identifier that does not allow for identification will not be personal data under GDPR. Emerging consumer neurotechnologies present a very complex case of personal data processing. Based on the foregoing material, along with Recital 26 it appears that only completely anonymized data could qualify as non-personal data, as only anonymizing this data would prevent data subjects from being identified.
While on the face of it, neurotechnologies deal in recordings of electrical signals from brains, what they produce ought to be considered personal data under the scope of data protection regulation. What remains is a debate over how significant this data may be, how existing regulations should be interpreted, and what additional regulation may be required.
It is unquestionably processed in terms of the GDPR. It is also personal because it is an identifier of a data subject, either on its own or through linkage with other data. It also appears to be highly significant information that could be classified as sensitive. This raises the possibility that repurposing existing data sets may result in the identification of subjects who were previously unidentifiable at the time the data was collected.
Although there are many questions about how unique a user is in these databases and how much information can be deduced about them, it is undeniably true that this information relates to an individual’s most private sphere and, as such, must be legally protected from indiscriminate dissemination.
Thus, in the GDPR and other existing data protection frameworks around the world, the lack of strict rules limiting the opportunities for using EEG data clearly risks infringing upon the fundamental rights of individuals. Indeed, the right to health is contingent on the assurance that no brain data will be made available to third parties who could use it to harm the data subject. In other words, brain data protection is a condition sine qua non for any individual who wishes to protect not only his or her private lives but also his or her freedom.
Conclusion
The primary motivation for the author to write this article stems from a simple thought: “what if” the main law, which is supposed to protect individuals when they share personal data, simply lags behind technological advancements? After all, we know from experience that what we thought was science fiction a decade ago becomes science fact of today.
The description of the BCI’s technical operation has provided insight into why bridging gaps in the existing data protection legislation is necessary. Not only because the output of a BCI is dependent on an input of brain activity data, but also because EEG data is very multi-dimensional. Therefore, from inferring legal issues from today’s problems to the possible applications of neural devices in the future, we expect many challenges to the legal system, including Data privacy and Cybersecurity. Device manufacturers and service providers might have deep and unique access to the information stored inside the brain, hence they need to have intensive data security policies to set-up checks and controls over the manufacture and the service provider that supports such devices. Similarly, they will also need privacy policies to manage operations relating to sensitive data and systems. Laws need to lay out security and privacy requirements on manufacturers of these devices and the companies that service them, as there may be lawsuits arising from privacy breaches and the violation of security and privacy requirements in statutes and regulations.