Ed. Note.: This post, by Sayan Bhattacharya, is a part of the NALSAR Tech Law Forum Editorial Test 2016. Search engines which are quintessential to our internet experience are mechanisms of indexing and crawling through data to provide us with a list of links which are most relevant to both our present and past searches….
Category: 101s
The Right to Be Forgotten – An Explanation
Ed. Note.: This post, by Ashwin Murthy, is a part of the NALSAR Tech Law Forum Editorial Test 2016. The right to be forgotten is the right of an individual to request search engines to take down certain results relating to the individual, such as links to personal information if that information is inadequate, irrelevant…
AADHAR AND THE RIGHT TO PRIVACY
Ed. Note.: This 101, by Vishal Rakhecha, is a part of the NALSAR Tech Law Forum Editorial Test 2016. The Aadhaar (Targeted Delivery of Financial and Other Subsidies, Benefits and Services) Act, 2016 or simply the Aadhaar Act passed in the Lok Sabha to facilitate the transfer of benefits and services to the individuals. This…
TORRENTS: THE LEGAL RAMIFICATIONS
Ed. Note.: This 101, by Kaustub Bhati, is a part of the NALSAR Tech Law Forum Editorial Test 2016. Have you ever used a torrent to download something not available freely? You must have. Ever wondered how it works and why there is so much fuss about it being illegal and people using it might…
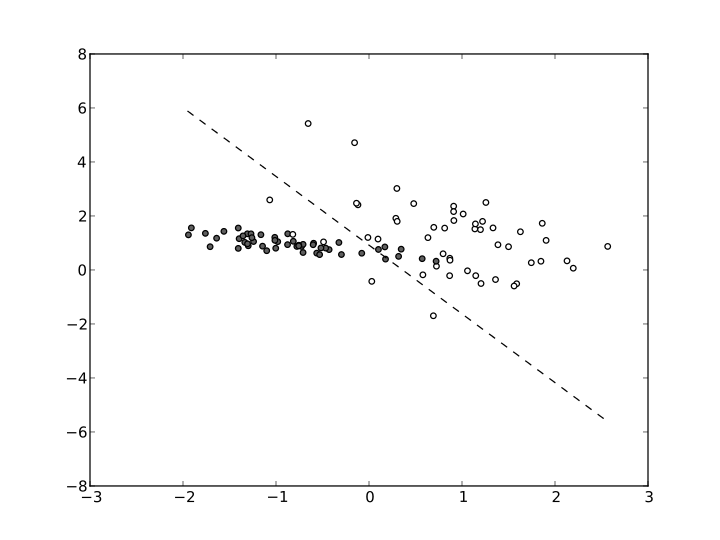
Machine Learning: An Explanation
Have you ever wondered how the spam in your mailbox is automatically detected? And what about speech recognition or handwriting recognition? These are quite challenging problems. But luckily they have one thing in common – that is data, and a good deal of it. Machine learning aims at creating systems that learn from data using various computer science…
Battling Goliath: An Analysis of the National Privacy Principles (Part I: Principles One to Four)
(Image Source: https://flic.kr/p/igPaVp) This is the first in a two-part post on the National Privacy Principles(NPPs). This post provides with a bit of background, and then deals with Principles One through Four, while the next will deal with Principles Five through Nine. Footnotes are especially important. Disclaimers: The first post is a bit on the longer…
Battling Goliath: An Analysis of the National Privacy Principles (Part II: Principles Five to Nine)
(Image Source: https://flic.kr/p/igPaVp) This is the second in a two-part post on the National Privacy Principles. This post deals with Principles Five through Nine. Footnotes are especially important. Disclaimers: I have taken a bit of artistic license with these two posts, so do allow for that. Feedback, comments, recommendations, are welcome. Following up on the previous post,…
The Concept of a Software Patent in India
Image Source (9 to 5 Mac, available at http://goo.gl/igU7Bd) A new challenge to the legal profession, particularly in the domain of intellectual property rights, has been that of examining the idea of a software. New software, with varying levels of originality or innovation is created every day. If you made one unlike anybody else ever had…
Intermediary Liability – An Explanation
(Image Source: https://flic.kr/p/o9EcaJ) Definitions and Explanations – the Concept of ‘Incentives’ An intermediary is an internet-based service provider, which provides its users with a platform to upload all and any types of content, ranging from text to videos. Some of the more popular examples of intermediaries would be Facebook, YouTube, Twitter, WordPress and Blogspot. The…
The Right to Be Forgotten – An Explanation
(Image Source: https://flic.kr/p/9RovZB) This is the first in a two-part post on the Right to be Forgotten. This post is part of our 101 series of posts, which seek to explain the issue at hand, and the next post shall address the issue and the debate surrounding it in more detail. In 2010, a Spanish citizen filed a complaint…